Adding a security group to the Local Administrator Group in AD

[su_tooltip position=”north” content=”Note: I normally disable the built-in Administrator account., and make another account an admin. This is a good security precaution and in my opinion a best practice.”][/su_tooltip]
Having a local administrator of your workstations can come in handy. Sometimes you might need to logon locally to troubleshoot or rejoin a computer to your domain. You can create a group policy that creates a local admin users and sets the local password.
Admins make a common mistake when they want to add a security group the Local Administrator group for a particular set of machines or domain wide. The mistake they make is creating a restricted access group vs. just adding to the existing Administrators Group. The result it that it wipes out any existing Local Administrator permissions or memberships.
This can be accomplished with a Simple GPO.
I will cover both methods for clarification. First I will cover the correct way to add. The Second Method is how to add a restricted group.
Correct Way
CREATE THE SECURITY GROUP
- Open Active Directory Users and Computers
- Select your Security Group OU
- Right Click and select New > Group
- Give the Group a name, I used “AUTOMATIONâ€
CREATE THE GPO
- Launch Group Policy Management Console.
- Right click the OU that you want the GPO to apply to.
- Select “Create a GPO…â€
- This will Launch Group Policy Editor.
- Navigate to: Computer Configuration\Preferences\Control Panel Settings\Local Users and Groups
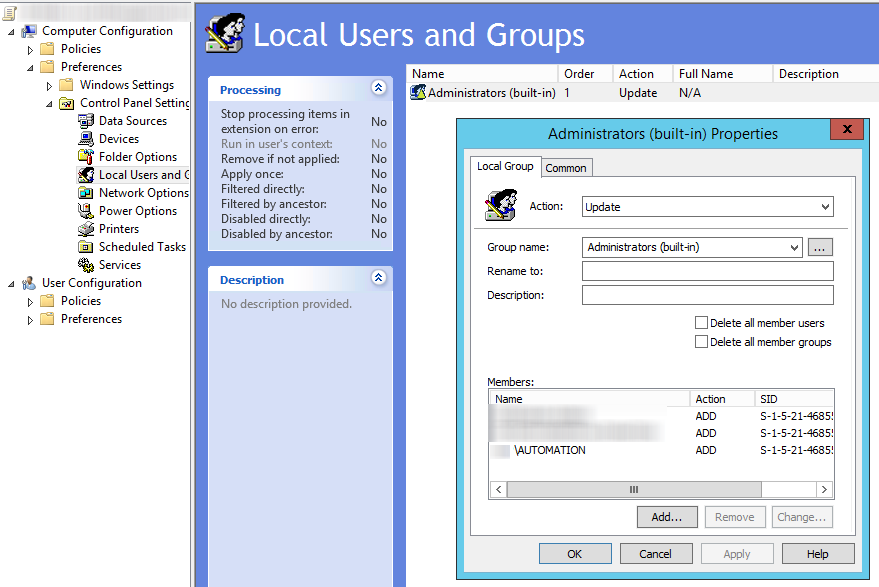
- Right Click in the blank area and select New > Local Group > Administrators (Built-in)
- Action: Update (This is the most important part).
- Add the needed security group. I have added my AUTOMATION Security Group.
- Click Apply.
- Click OK.
- Apply the GPO to the root of the domain OR the appropriate OU.
Incorrect Way (This is how you would create a Restricted Access Group)
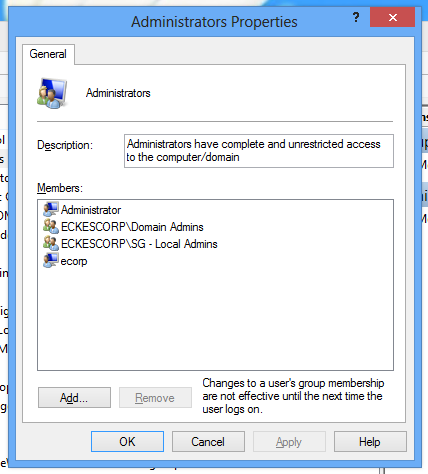
[su_note note_color=”#ee899a”]Reason this is incorrect: This will wipe out any existing memberships of the Local Administrator Group. [/su_note]
If you want certain members to be local administrators of computers, you can do it through Group Policy. The idea here is to create a Local Admin security group and then a GPO that adds that security group to the local Administrators group of the computer.
CREATE THE SECURITY GROUP
- Open Active Directory Users and Computers
- Select your Security Group OU
- Right Click and select New > Group
- Give the Group a name, I used “SG – Local Adminsâ€
CREATE THE GPO
- Open Group Policy Management Console.
- Right click the OU that contains the systems you want to set the local admin on
- Select “Create a GPO in this domain, and Link it here…â€
- Name the GPO. I used “Set Local Administratorsâ€
- Right Click the GPO and select Edit.
- Set the following:
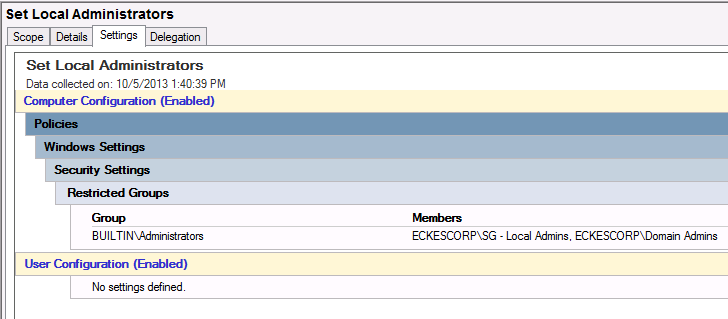
- Computer Configuration\Policies\Windows Settings\Security Settings\Restricted Groups
- Right Click and select “Add Group…â€
- Select browse and add the Administrators group
- Select OK
- Double click Administrators
- Select Add for “Members of this group:â€
- Browse and find your security group. I added “SG – Local Adminsâ€
That should be it. Now you can set which users of the domain are local administrators of their computers.
Author
Related Posts

Get all the domains controllers in the AD forest along with their current FSMO roles
In a large enterprise an admin would need to keep track of all the domains in a AD forest, the domain names,...
Read out all
Force synchronization for DFSR-replicated SYSVOL
One of my clients had a problem with processing GPO on client computers. Different computers applied different settings from the same GPO...

Get Inactive Users Report for the past 60 days in a multi domain environment
I had a request recently to provide an inactive user report for the past 60 days. Basically, find out which accounts have...

Get Primary, Secondary, Tertiary DNS values and more from Multiple Servers
Came across a unique request to get primary, secondary, and tertiary DNS values for multiple computers/servers across the domain. I started writing...

Fix Active Directory broken security inheritance problem
Ran into a situation at a client location where in Active Directory, the security permissions applied to an OU were not getting...
How to Fix: Attribute userAccountControl of DC is: 0x82020
When running a DCDiag at a customer site today I had the following error occur: [su_box title=”” box_color=”#f3f1cb” title_color=”#000000″ radius=”6″]Warning: Attribute userAccountControl...
1 comment
Comments are closed.